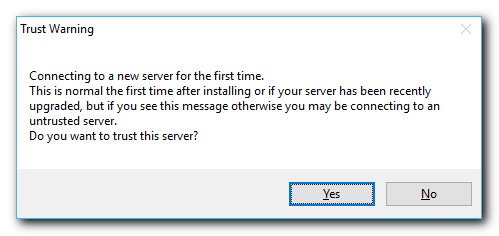
Trust Warning
Use KeePass with Pleasant Password Server
When connecting to a new server, KeePass will prompt to confirm Trust in this new server. Once a secure connection has been properly established this message should not display again, except in the case of configuration changes.
Related topic:
Repeated Certificate Warnings
If you keep seeing repeated Trust Warnings each time you open KeePass, but not with the web client, you may have a problem with the certificate on your workstation.
The most common reasons are:
- Problem with the Certificate location in the Certificate Store (most likely)
- Problem with the Certificate
- A URL in the certificate cannot be reached for CRL/OSCP validation
- May be blocked by firewalls/filters
- Server has been migrated recently
- Network Connections have changed
- Security Policy problem
Follow these steps:
- Check if there are Certificate problems
- Server Migrations: if you have recently changed your networking or migrated a server, the URL(s) listed in the Certificate may be pointing to a location that no longer exists: ensure that the URL locations are still valid for Certificate Status checks (see bottom section).
- Check that Pleasant Server has not been interrupted: Restart the Service
- If you continue to have problems, please let us know: your steps and your results and send your Detailed Log files (Server, Web & KeePass) to Support.
- We will take a look and diagnose the problem and can schedule a screen-share to resolve if necessary.
Certificate Store Locations
If your Certificate is properly installed on the workstation, it should be trusted because it will be stored in the Certificate Store.
KeePass for Pleasant client saves this in the Certificate Store:
-
User Certificates: Trusted People
KeePass for Pleasant client also looks in this location in the Certificate Store:
-
Computer Certificates: Trusted People
On the Password Server machine, this certificate is placed in the Certificate Store:
-
Computer Certificates: Computer Personal Certificates
The Certificate Store can be opened with:
- Windows Server:
- Manage Certificates (MMC)
- Windows 10:
- Type Certificates into Control Panel / Windows Search
- Manage computer certificates
- Manage user certificates
- Type Certificates into Control Panel / Windows Search
Viewing Certificates from the Browser
To view the details of your certificates and check them for errors, it's possible to check them with your browser:
In Chrome:
-
Type F12 on a browser page -> Click Security tab -> Click View Certificate -> Click Details tab
In Firefox:
-
Click lock beside the URL -> Click ">" to view connection details -> Click More information -> Click Certificate(s) to expand a list (if there are more than one) -> Click Security tab -> Click View certificate -> Click Details tab
Standard Certificate Checks
- (Client-Server Connections) Test if other connections have a problem:
- Connecting to our private free-to-use Demo Server, OR,
- https://www.pleasantsolutions.com/PasswordServer/Demo.aspx
- Connecting using a mobile device with a which has the same certificate, and which has connection access to the Password server to see if the mobile app / browser can connect successfully
- Connecting to our private free-to-use Demo Server, OR,
- Check that the Certificates are stored in the Certificate Store in the proper locations
- Check that the Certificates have not expired
- Check that the Certificate "Issued To" exactly matches the server location address
- Check that the Certificate "Issuer" information is correct
- Check if the SAN field should be included
- Check that the certificate has a trusted root Certificate Authority (CA) - import that certificate into the Trusted Root CA location
- Check the CRL Distribution Point information is still valid
- Check that the Certificate is not using an old SHA1 signature hash, and is properly switched to SHA256 / SHA512
If there a Certificate problem remains, continue on to the more advanced checks below.
Validate Certificates with CertUtil
You may wish to validate your certificate using a utility such as:
- CertUtil (installed with Windows)
- DigiCertUtil
This CertUtil command line utility can provide information about the store certificate(s), with simple commands such as:
- certutil -verifyStore MY
- certutil -p MyCertPassword -dump MyCertificate.pfx
- certutil -verify -urlfetch <MyCertificate.pfx>
Other commands that may be useful:
- certutil -?
- certutil -store my "63973106d160ae38db474fc7fe94fbf918bffe01"
- certutil -v -store my "63973106d160ae38db474fc7fe94fbf918bffe01"
- certutil -user -store my "63973106d160ae38db474fc7fe94fbf918bffe01"
- certutil -csp "Microsoft Software Key Storage Provider" -key
Certificate Status Checks
Beginning with the Root Certificate, the Certificate chain is validated, looking for any revocation statuses on the certificates.
If the machine does not have access to the URLs mentioned, this status check will fail. This is found here:
- CRL: CRL Distribution Point attribute
- OSCP: or under Authority Information Access > Alternative name
There are 2 methods of checking certificate statuses: CRL & OSCP
- OSCP - Status stapling: (Has largely replaced the below method.) The client queries a URL requesting if the certificate is revoked or not.
- CRL - Revocation Lists: A list of certificates revoked before certificate expiry.
For more information:
Test your cert status URL's:
- ping the urls or ip addresses
- certutil -verify -urlfetch <MyCertificate.pfx>
Here is a full list of validation items for revocation statuses:
- Chained certificates may have expired or are not yet in effect
- The Certificate may not have been issued for current use
- Invalid name, constraints, or policy
- The Certificate Authority (CA) may no longer be trusted
- Root Revocation may be unknown when determining certificate verification
- The Certificate Authority Revocation may not be specified
- The End Certificate (i.e. the user certificate) revocation is unknown
- The Certificate Trust List (CTL) signer revocation may not be unknown
- The Certificate Trust List (CTL) may not be valid or is expired
- Together the CA (Certificate Authority) certificate and the issued certificate must have nested validity periods
