Client Certificate Authentication
Website Documentation for your KeePass client and Pleasant Password Server
(Versions 7.9.0+, Web & KeePass clients)
Client Certificate Authentication is an advanced security mechanism allowing connecting Clients to prove their identity to a Server by providing a Certificate. This can be accomplished by configuring IIS to require an established Certificate from the connecting devices.
Requires:
- Setup of IIS (7.5+) to host Password Server
Step-by-Step Reference for Configuring IIS for client certificates
Here the manual steps for configuring your IIS site to map certificates.
This steps are technical and quite involved, and need to be followed closely to ensure something is not missed.
Configuring KeePass for Pleasant Client
Here is a technical summary of how the functionality works:
-
The Client will establish a TLS/SSL session with IIS, and send a request. IIS sends a new TLS/SSL request to re-negotiate based on the client certificate authentication, and asks for a certificate. Once provided by the client, the second TLS/SSL negotiation completes successfully.
-
To set the option, open this KeePass config file:
- %appdata%\PleasantKeePass\PasswordServerClientConfiguration.xml
-
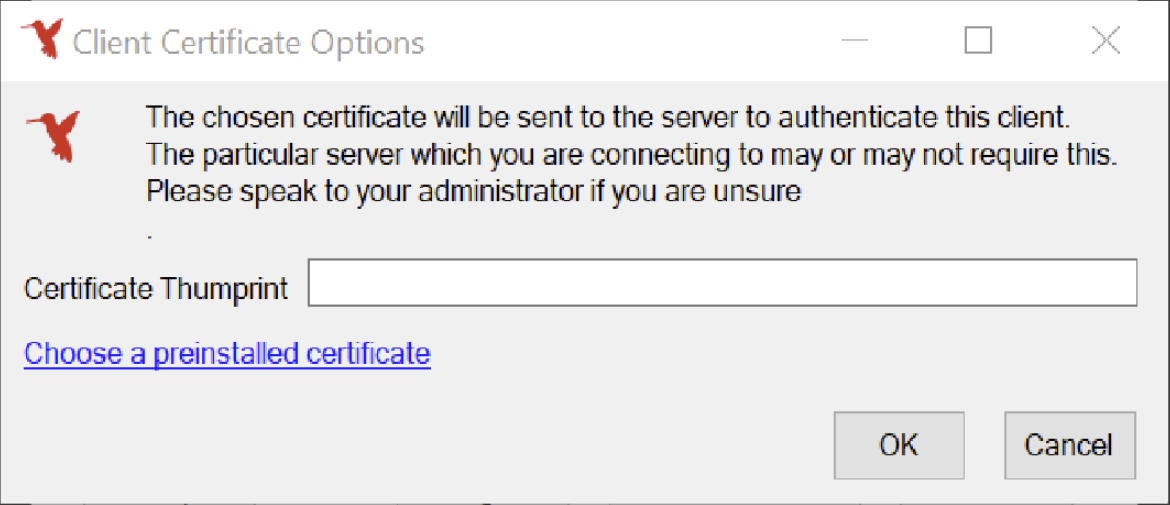
Look for the Thumbprint on your client certificate. Add a line called ClientCertThumbprint so that the file includes lines that look similar to this:
- <CertThumbprint>801F5DE467D0365B14935A53FA4A43EC48AEB3C6</CertThumbprint>
- <ClientCertThumbprint>AC538GE891D4B123A3432FB5B51ED51BCE4A1129</ClientCertThumbprint>
Using Client Certificate Authentication
When KeePass opens, a user can click Advanced Options
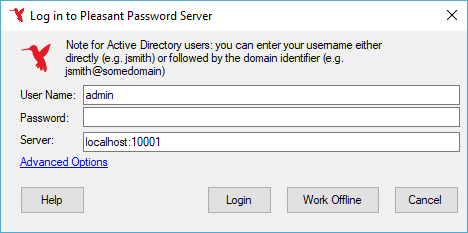
To choose another Certificate a user can select one from their Certificate Store, or enter a Certificate Store